When you are the target of a touch attack your AC doesnt include any armor bonus shield bonus or natural armor bonus. Downgrade attacks in the TLS protocol take many forms.
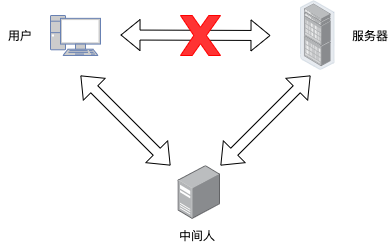
从无法访问github到中间人攻击 Ghosind
Ssl中间人攻击 是怎么回事 归航 龙泉墨客的驿站

China Gov Runs Mitm Attack On Google Userssecurity Affairs
He has big green eyes red and gold feathers and purple tail feathers.

Man in the middle 攻撃. The Nagasaki Buzzard Attack Chopper formerly named Buzzard is a light attack helicopter featured in The Ballad of Gay Tony Grand Theft Auto V and Grand Theft Auto Online. Learn more about man-in-the-middle attacks. Country Total Cases New Cases Total Deaths New Deaths Recovered Active Cases Critical Cases.
Sybil Attack is a type of attack seen in peer-to-peer networks in which a node in the network operates multiple identities actively at the same time and undermines the authoritypower in. He shares the exact HP values at both minimum and maximum with Kingprotea. GP Games Played W Wins L Losses MIN Minutes Played OFFRTG Offensive Rating DEFRTG Defensive Rating NETRTG Net Rating AST Assist Percentage ASTTO Assist to Turnover Ratio.
中間者攻撃mitm マンインザミドル攻撃 バケツリレー攻撃とは暗号通信を盗聴したり介入したりする手法の一つ通信を行う二者の間に割り込んで両者が交換する公開情報を自分のものとすりかえることにより気付かれることなく盗聴したり通信内容に介入したりする手法. Phoenix Man is a tall bird that resembles a phoenix. An ad hominem argument is often a personal attack on someones character or motive rather than an attempt to address the actual issue at hand.
There are 198 movies 60 shorts and 4 specials in the MST3K canon. In cryptography and computer security a man-in-the-middle monster-in-the-middle machine-in-the-middle monkey-in-the-middle meddler-in-the-middle MITM or person-in-the-middle PITM attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other as the attacker has. Emily Petty 16 suffered from PTSD and needed counselling.
Wanda Maximoff also known as Scarlet Witch is a native of Sokovia who grew up with her fraternal twin brother Pietro. At the scene a Syrian passport was found which bore this name suggesting the man was a 25-year-old from the Syrian city of Idlib but authorities believe this passport was a fake. The Buzzard is evidently based on the AH-6 an attack variant of the MH-6 Little Bird light observation helicopter which in turn is a military version of the OH-6 Cayuse and the MD 500C.
After his first resurrection his costume turned into a suit. The lethal dose for humans of such toxins is in the sub-microgram range which is many times lower more toxic than the dosage for nerve agents. When you attempt to dock at the Illusive.
This allows them to intercept information in both directions and is commonly called a man-in-the-middle attack. Botulinum toxin is the most toxic agent known ever to man and is a very potent neurotoxin which blocks the release of AChE from the cholinergic nerves of the human nervous system. See Notes below for help on using this page.
He is made obtainable after The Old Man of the Mountain Summoning Campaign. This article describes various types of security attacks and techniques to mitigate them. This mission is acquired immediately after the events at Sanctuary.
Downgrade attacks have been a consistent problem with the SSLTLS family of protocols. MITM攻撃はMan in the middle attackの略語中間者攻撃とも呼ばれる二者の通信に第三者が割り込み通信内容の盗聴や改ざんを行う攻撃を指す. Once the attack is launched the Alliance will be fully committed to the final fight against the Reapers.
With MITM attacks the criminal positions themselves between your device and the server. Click-jacking is the practice of tricking a user into clicking on a link button etc. The Old Man of the Mountain is an NPC only in Camelot and an NPC-Support only in Babylonia.
Born with the latent mythical ability to harness Chaos Magic she developed a hatred against Tony Stark and rallied anti-American protests after the Novi Grad Bombings killed her parents. In a real attack this would be done by an active man-in-the-middle but a passive man-in-the-middle can also mount the attack -- it will just take more time to collect the data. Phoenix Man フェニックス男 Fenikkusu Otoko is a Mysterious Being and a member of the Monster Association.
Mystery Science Theater 3000 19881999. An attacker can also opt to hijack the session to insert themselves between the requesting computer and the remote server pretending to be the other party in the session. It also features a FLIR Forward.
The Old Man of the Mountain was available for summoning during the. His Noble Phantasm Azrael is the only one which can skip an enemys death. An ad hominem argument or argumentum ad hominem in Latin is used to counter another argument.
Man-in-the-middle MitM Session hijacking. Examples of such attacks include the POODLE attack. 代表的な攻撃手法の例としてネットワーク上のプログラムとサーバーとの間に攻撃者が侵入介在するMITMMan in the middle attack攻撃やDNSサーバーのキャッシュ機能を悪用して偽のDNS情報を問い合わせたユーザーに返信させるDNSキャッシュポイズニングなどがある.
Years later in an effort to help purge their country of strife the twins joined HYDRA. This page is not complete. Detection of these attacks is difficult but prevention is possible.
They eavesdrop on intercept and manipulate communication between two parties this often happens on unsecured wireless networks such as public WiFi. Some attacks completely disregard armor including shields and natural armorthe aggressor need only touch a foe for such an attack to take full effect. He held a middle management position under the association outranked only by the executives.
Downgrade attacks are often implemented as part of a Man-in-the-middle MITM attack and may be used as a way of enabling a cryptographic attack that might not be possible otherwise. 公開日20200107 最終更新日20200813. The Illusive Mans headquarters have been located and the Alliance is prepared to attack to recover the Prothean VI that holds the key to the Catalyst.
However its based on feelings of prejudice often irrelevant to the argument rather than facts reason and logic. In these cases the attacker makes a touch attack roll either ranged or melee. 20172018 is an American TV show that mocks bad movies by riffing on their strange characters absurd settings and silly plot twists interspersing erudite cultural quips with schoolboy jokes and general zaniness.
中間者攻撃Man In The Middle Attackとは仕組みや危険性対策について徹底解説. OWASP is a nonprofit foundation that works to improve the security of software. A teenager who survived the Manchester Arena bomb has achieved the GCSE grades she needs to continue her dream of becoming a dancer.
Attacks on the main website for The OWASP Foundation. Assault the base when ready. Proof-of-Concept Attack Demo In our setup we use Firefox Developer Edition 470a2 running on Linux and an IIS 60 server in a Windows Server 2003 R2 SP2 Virtual machine.
一文了解 中间人攻击 Mitm 附防范建议 嘶吼roartalk 回归最本质的信息安全 互联网安全新媒体 4hou Com

如何避免中间人攻击 Mitm 51cto Com

编程吃瓜 什么 吴签被 中间人攻击 知乎

Man In The Middle Attack 中间人攻击为什么需要ca 认证机构颁发证书 Rsapaper Ing 博客园

网络犯罪分子利用中间人攻击窃取登录信息

什么是中间人攻击 Mitm攻击解释 Malwarebytes Lawww Vwincn Combs Malwarebytes Labs 66vwin
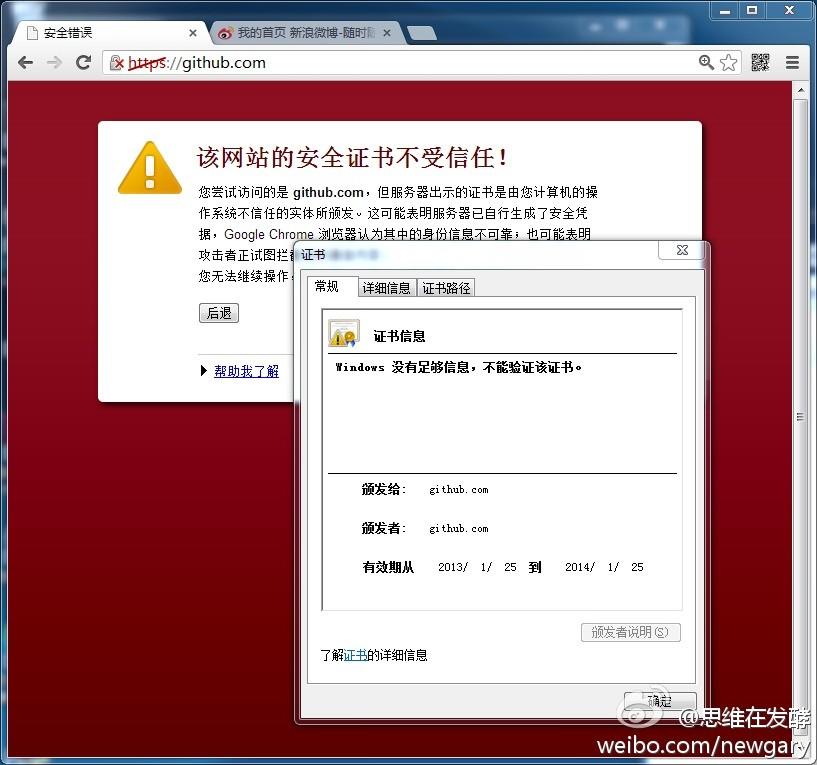
中国 Github 和中间人攻击 Greatfire Org

网络安全之中间人攻击 每日头条
